16 Billion Leaked Passwords: Unpacking the World’s Largest Alleged Data Breach
This month, cybersecurity researchers have uncovered one of the largest data exposures to date: 16 billion login credentials spread across 30 datasets. The breach appears linked to infostealer malware, a type of malicious software that silently infiltrates personal devices and extracts all kinds of data from login details and session cookies to browser history and saved credit card information.
The leaked credentials in the massive breach span a wide range of services, including Google, Facebook, Apple, GitHub, and even government platforms.
The Controversy: Are 16 Billion Credentials Really at Risk?
The datasets contain billions of records, structured in the typical URL:username:password format used by infostealers. Many entries also include session cookies, authentication tokens, and browser autofill data, making them useful for bypassing even two-factor authentication (2FA). One dataset alone contained over 3.5 billion records. Others included platforms like Telegram, Zoom, and various VPN providers, including both personal and enterprise tools.
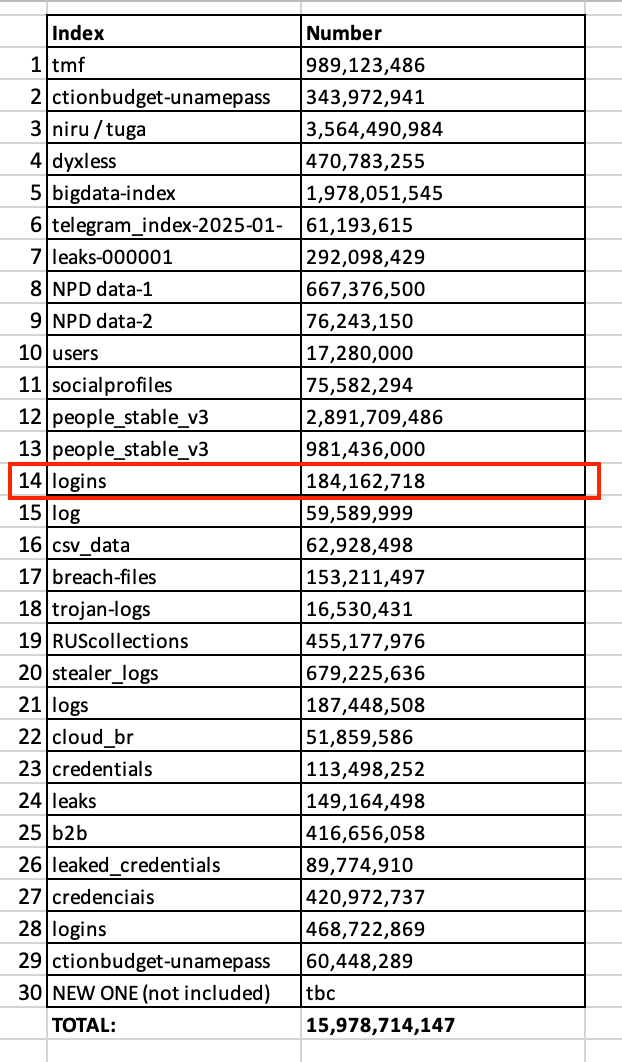
Image Source: Cybernews
However, there is disagreement among experts about the exact nature of the breach.
Critics argue that the original report by Cybernews was based largely on three screenshots and minimal context, with limited technical evidence to support claims of a singular, historic breach. Cybersecurity professionals, threat analysts, and digital forensics experts quickly pointed out that much of the dataset appears to be a compilation of old, recycled infostealer logs rather than a newly discovered or coordinated attack. This is supported by the presence of duplicate entries across datasets and the likelihood that some credentials are outdated or already inactive.
Others argue the breach includes recent data, pointing to active session tokens, intact metadata, and modern site references as evidence. The structure and recency of many records suggest that at least part of the dataset contains valid, active credentials.
The total number of unique credentials remains unclear. Because of the volume and overlap, there’s a big chance that a lot of the records were duplicates. But even if only 1% of them are valid, that would still mean at least 160 million compromised accounts.
What’s at Stake
Regardless of exactly how much information really got leaked, this incident is a reminder of the slow, ongoing nature of data breaches. Instead of just isolated events, they often involve continuous siphoning of personal data through poorly-secured systems. Once devices get infected, infostealer malware extracts every saved login on the device and sends it to criminals who may sell or exploit the data later.
This puts users in low-security environments, such as those using shared computers, outdated antivirus software, or the same password across services, at serious risk. A single compromised login can lead to identity theft, financial fraud, or business email compromise.
What makes matters worse is that many companies don’t monitor for this kind of breach. Victims may not realize their information has been stolen until it’s too late.
How Blockchain and Decentralized Identities Can Help
This breach exposes a fundamental flaw in today’s digital security infrastructure: centralized identity systems. In most cases, users rely on usernames and passwords that are stored on company servers. These central databases become single points of failure, which, if breached, can affect millions of people at once.
Blockchain technology offers a fundamentally different approach through decentralized identity and authentication. Rather than handing over your credentials to every website you visit, blockchain-based systems such as zero-knowledge proofs allow you to prove ownership of an identity or credential without revealing sensitive information.
Take the example of logging into a website. In the traditional model, you enter a password that gets checked against a centralized server. If that server is compromised, so is your password. In a blockchain-based system, you’d use a private key stored locally on your phone or hardware wallet to cryptographically sign a login request. The platform verifies the signature using a public key, but it never sees or stores your actual private key or password. In effect, you’re proving that you own your identity without having to show your password at all.
This model is already being explored through technologies like:
- Passkeys – biometric-based credentials tied to your device, using public-key cryptography instead of passwords.
- Verifiable Credentials (VCs) – digitally signed statements (e.g., “this person is over 18”) issued by trusted authorities that users can present without revealing full identity.
- Self-Sovereign Identity (SSI) – a user-controlled framework where identity data lives in your hands, not in company databases.
A good analogy is digital passports which allow you to pass through airport security by presenting a signed proof that you’re cleared to fly, without ever handing over your full passport. That’s the kind of selective disclosure blockchain enables.
These systems remove the target that hackers usually aim for. If no passwords are stored on a server, there’s nothing for infostealers or data breach attackers to steal. Instead of defending a fortress (central server), the security is distributed and each user holds their own key.
Of course, decentralized identity standards are still evolving, and mainstream adoption is slow. Most platforms still rely on conventional login methods, and users often prioritize convenience over security.
Still, this breach reinforces why these innovations are necessary. As infostealer malware becomes more common and credential leaks grow in volume, blockchain-based identity solutions offer a proactive way forward, instead of just waiting before the next breach happens.
.svg)


.svg) SHARE TO FACEBOOK
SHARE TO FACEBOOK SHARE TO TWITTER/X
SHARE TO TWITTER/X SHARE TO LINKEDIN
SHARE TO LINKEDIN SEND TO MAIL
SEND TO MAIL





.svg)


.svg)